Social media mercenaries exposed.
As US extradition case hearings loom, documents reveal new facet of sophisticated intelligence gathering operations against Julian Assange and supporters.
How vast is the US-led intelligence operation targeting WikiLeaks? To whom was ex-CIA Director Mike Pompeo referring when he coined the phrase ‘Assange and his ilk’? Talk Liberation Investigates…
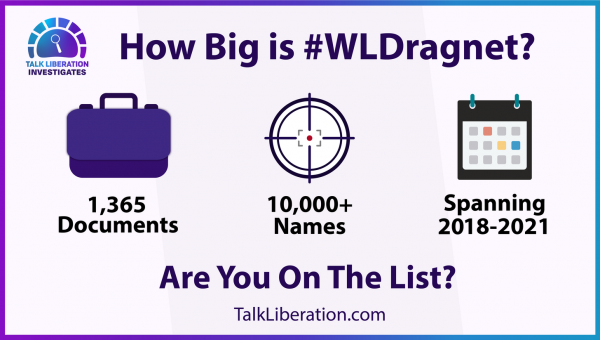
New evidence derived from publicly available data points to a global network of digital repression being targeted at WikiLeaks supporters: with hundreds of social media accounts named, thousands collected on.
Documents uncovered by Talk Liberation reveal a new facet of the public surveillance operation against WikiLeaks: how data sciences and social media monitoring coalesce to identify and compile what are effectively target lists of the most prolific and impactful supporters of Julian Assange. The documents are focused on crucial moments in modern history, including the expulsion of Assange from the Ecuadorean Embassy on April 11th, 2019.
In this reporting Talk Liberation details:
* which WikiLeaks supporters and commentators have been pulled into this social media dragnet
* who is behind the entities involved in producing these network maps
* how data like this is easily utilized by corporations, intelligence agencies, militaries and governments in potentially dangerous ways
In service to public interest journalism, Talk Liberation Investigates is releasing the multi-source document set, a technical report and related investigative materials in this public file repository, contributed to and curated by the co-authors of this original work: Sean O’Brien, Founder of Privacy Lab at Yale Law School and Chief Security Officer at Panquake.com, and Suzie Dawson, Founder and Chief Product Officer at Panquake.com
For Julian Assange and those closest to him, the journey to the Royal Courts of Justice this week has been arduous and fraught with nail-biting intrigue and danger. Scheduled to appear on October 27 and 28, Assange will be subjected to a US appeal against an earlier judgement by a lower Court that found in his favor. While the US attempt to strike down the previous finding again places Assange in grave peril, this time the passing months have played in his favor, as growing support for the WikiLeaks publisher has invigorated and swelled the numbers of various grassroots campaigns demanding his freedom.
Assange’s lawyers will arrive armed with statements in support by 25 leading press freedom and human rights organizations, calling in unison for an immediate end to the more than decade-long multi-jurisdictional lawfare waged against the Australian journalist.
In 2020, shocking revelations of CIA contractor UC Global’s human intelligence operation against Julian Assange, WikiLeaks and close associates shed light on invasive and illegal physical and electronic spying methods wielded against the world renowned publisher. During what would prove to be the waning months of Assange’s refuge inside the Ecuadorean Embassy in London where he had resided since 2012, every movement made and every conversation had, including legally privileged conversations with his lawyers, was collected and delivered into the eager hands of the US-based masterminds of Assange’s unprecedented transnational persecution.
The collateral damage of the spying operation was extensive: friends, colleagues, journalists, politicians, technical experts, Assange’s fiancée Stella Morris, their infant son and even her mother; all were ensnared in the UC Global dragnet. The pervasiveness of the methods employed demonstrate the willingness of US authorities to go to extraordinary lengths to obtain the most intimate details of Assange’s daily life. Yahoo News recently cited former top US counterintelligence expert William Evanina describing the product of the spying as an “exquisite collection of [Assange’s] plans and intentions”.
While state threats against WikiLeaks track back to as early as 2010, the agenda to destroy WikiLeaks has spanned multiple US administrations and across the years grew increasingly naked: with ex-CIA Director Pompeo, while being interviewed at the Aspen Security Summit in June of 2017, appearing emphatic in his assertion that Assange should be prosecuted under the archaic Espionage Act.
Sitting next to Pompeo, Bret Stephens of the New York Times raised Pompeo’s past criticisms of Assange and asked, “What does that, to your mind, imply? Legislatively or operationally. Should we be enforcing the Espionage Act much more?”
Before Stephens even completes the question, Pompeo interjects with a firm “Yes.”
“I’m quite confident that had Assange been around in the 30s, the 40s and the 50s, he would have found himself on the wrong side of history.” – ex-CIA Director Mike Pompeo
Preparation of the indictment against Assange and his subsequent prosecution are the province of the Department of Justice, not the CIA. The CIA’s business is in something else entirely.
At the Aspen Conference, Pompeo was more forthcoming regarding methods of targeting more traditional hostile adversaries, when speaking to his agency’s counterterrorism efforts against groups like Al-Qaeda and the Islamic State (ISIS). Of the latter, he said: “We’re going to have to work to pressure them, to provide CT [counterterrorism] pressure, in a way that CIA and DOD know how to do. We broke the back of Al-Qaeda. We crushed them. We didn’t do it by just taking down a handful of folks, we took down their entire network. We’ll have to do it again.”
When employed against an armed, military force that terrorizes unarmed civilian populations, such a hard line attitude emanating from a public figure can read as measured and justifiable. Indeed, in the absence of CIA drone bombings of weddings, of funerals, or of their international allies deploying US-manufactured weapons to blow up school buses in the name of pursuing counterterrorism, there might be little to no criticism at all.
But when military strategy, tactics and resources are deployed against unarmed non-combatant civilian targets, especially when those targets are employees of a news agency, such as the Reuters journalists slaughtered to the tune of mocking laughter from the cockpit of a US Air Force helicopter gunship, the unforgiving, self-perpetuating and immovable quality of counterterrorism-related rhetoric quickly loses its taste.
Similarly, Pompeo’s notorious pronouncement of WikiLeaks as being a “non-state hostile intelligence service” seemed designed to open the full suite of counterterrorism and counterintelligence options to the historically scandal-plagued intelligence agency.
The denouncement opened a gateway to a dangerous new chapter of persecution by proximity for those connected to Assange, in a relentless and ethically dubious campaign that has spawned multiple prongs of legal contention that will be hashed out once again at the Royal Courts of Justice in the coming days.
However, the true breadth and depth of the intelligence dragnet cast by those state and military agencies targeting Julian Assange and WikiLeaks, or how many citizens lives have been sucked into the undertow, has until now remained deep below the surface of mainstream reporting on the case.
It was ten years ago now, in 2011 that the first rudimentary social network mapping of WikiLeaks and their pillars of support hit the spotlight. Extensive mainstream reporting exposed myriad nefarious activities of black-ops intelligence companies like HBGary, who had strategized the targeting of key figures including Pulitzer Prize-winning journalist Glenn Greenwald in retaliation for his support of Assange and his journalism.
In a document titled The WikiLeaks Threat: An Overview authored by Palantir Technologies in conjunction with HBGary Federal and Berico Technologies, a slide centrally featuring the WikiLeaks logo depicts spokes leading to key public supporters. Notes at the bottom of the slide outline the corporate grievances in play, decrying “established professionals… with a liberal bent” and declaring that “this level of support needs to be disrupted”. The final line reads “without the support of people like Glenn, WikiLeaks would fold”.
What folded, in fact, was very nearly HBGary itself. CEO and minority shareholder Aaron Barr stepped down in disgrace.

It wouldn’t be the first time or the last that Greenwald would be targeted in some form for his journalism. That he is also named (and even central) in some of the new #WLDragnet documents, will likely come as no surprise.
Nor to the other influencers identified in the documents.
“It’s not surprising that the social media accounts of Assange supporters are being monitored by shady government-tied institutions. But seeing my name on their lists was still pretty freaky.” – Caitlin Johnstone (@caitoz), an independent journalist named repeatedly in the NodeXL #WLDragnet documents
A who’s who of high profile independent media, whistleblowers and support organizations who stand with Julian Assange and WikiLeaks are named again and again in the #WLDragnet documents.
As are thousands of their followers, members of their personal networks and frankly, damn near anyone with even the vaguest sense of political awareness or understanding as to the historic importance of the battle to save Julian Assange.
It has long been assumed by all and sundry that only WikiLeaks staff, closest collaborators or other persons of significance could be plausibly caught in such a web. That those possessing insider knowledge, occupying positions of some influence or power, or with the ability to extend significant social reach were the logical focal targets of state-led efforts to clip the wings of WikiLeaks.
But new evidence points to a truly global network of digital repression targeted at WikiLeaks supporters who possess little if any such secret knowledge, significance or power. The documents we are publishing, sourced from publicly available data, contain the social media user account handles of hundreds of members of the public, with thousands collected on.
“The toll on my mental health is probably the worst thing because you know you are up against a paid army of trolls who expose your personal data” – WikiLeaks supporter A, named in the NodeXL Embassy expulsion graph, speaking on condition of anonymity
Reports of targeting experienced by regular, everyday citizens in WikiLeaks’ extended support network have until now remained anecdotal, whispered in back channels on social media between trusted friends, or buried in obscure blogs. For the first time, Talk Liberation Investigates has obtained datasets which reinforce the long-held suspicions of many: that they too have become collateral damage in the snare targeting Julian Assange. We have spoken with a significant number of persons named in the documents, and their harrowing stories of online and physical surveillance, sabotage and persecution have strikingly similar qualities.
“What we see here is a chilling example of mass surveillance of Assange’s activist support network on social media. Activists are identified and clustered into groups to profile them, their affiliations, and their impact and influence on social media conversations.” – Sean O’Brien, cybersecurity expert and Fellow, Information Society Project at Yale Law School and co-author of #WLDragnet
The first document Talk Liberation Investigates obtained is an analytical study based on a dataset of 18,000 tweets from 11,849 Twitter accounts actively sharing information about Julian Assange during the “5-day 5-hour and 36 minute” period leading up to his April 11th, 2019 arrest from the Ecuadorean Embassy in London. In the course of our investigation, we have come to refer to this document as the “Embassy expulsion graph”.
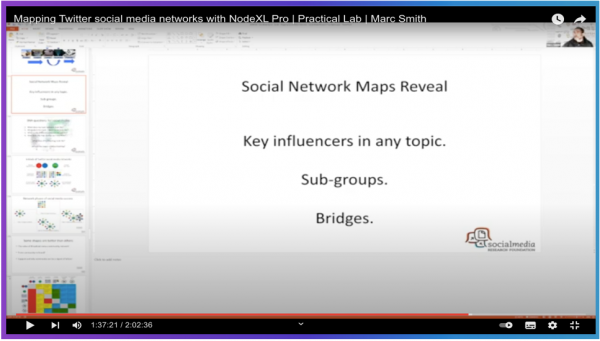
The document is the product of social network analysis: it is comprised of 60 highly sophisticated and intricate sub-graphs grouping a combination of both commonly known and arcane, geographically disparate and highly particular keywords and hashtags into curious and yet relevant clusters. Headed with a series of graphical representations of these sub-networks, group influencers including journalists and media organizations are organized into a series of ‘Top 10’ lists reflecting their centrality, “betweenness” and ultimately, their effectiveness.

Those with the largest output, reach and engagement sit at the apex, constituting clear marks in the extended support network of the world’s most targeted media organization: WikiLeaks. The hyperlinks (URL’s) that users share between each other and the domains hosting those links are also listed, as well as the most popular hashtags. Numbers of replies, mentions and retweets are factored in, although reach is not the sole metric for whether a user makes a ‘Top 10’ list or not.
“Sometimes people have the right spot on the landscape and even if they don’t have a lot of followers they have influence. So yes, some people are hubs, they are at the center of many connections. But hubs are not the only very important location to occupy in a graph. Some people could have, for example, 2 connections, while a hub has 200. And those 2 connections might be worth more than the 200 connections.” – Marc A. Smith, NodeXL Chief Evangelist
When we received the NodeXL Embassy expulsion graph, we didn’t immediately leap to the conclusion that it was generated by a force hostile to WikiLeaks or its supporters. Instead, we gave it the benefit of the doubt. Because we were aware that NodeXL can be used for legitimate purposes and has been many times, even by allies and as far back as during the Occupy movement.
It seemed feasible to us that the Embassy expulsion graph had been generated by an academic observer, an enthusiast or even a WikiLeaks supporter. Until we examined it more closely.
The first clue lay in the graph’s description: it was generated at 10:26am on April 11th, 2019. We did some checking and discovered that that was exactly six minutes after Julian was expelled from the Ecuadorean Embassy.
The next clues that the graph may be more than first met the eye, were the keywords selected to populate each subgraph. While a WikiLeaks supporter or enthusiast would absolutely know to select the keywords that appear in figure G1 (keywords like WikiLeaks, Assange, UK, Ecuador etc), there is exponentially less chance that they’d know to select keywords like Persvrijheid in G5; constitución onu asilo urgente in G6; londres and equateur in G8; botschaft in G11; yttrandefrihet in G15, and so on and so forth.
The inclusion of Beijing and China in figure 7 lends additional weight to what had become obvious: this was a sophisticated, professional undertaking with a very high entry barrier… by a person or persons exhibiting extraordinary knowledge of how to effectively span multiple geographical regions and languages to encapsulate the entire global support network of Julian Assange.
Their inclusion of the keywords brexit in G3, inapapers in figures 6 & 7 and donaldtrump in G16 indicate a clear political agenda to tie WikiLeaks supporters to each of the aforementioned, where possible.
More: their inputting of Assange supporter hashtags was chronologically accurate. Every reference to #Unity4J as a keyword in the subgraphs is preceded by the entry of #ProtectJulian. Both of those hashtags were founded by co-author of this article Suzie Dawson. #ProtectJulian was the fleeting (in duration) predecessor to what later became #Unity4J, and yet due to #ProtectJulian having trended in multiple countries, use of the hashtag persisted for months to follow.
Such a fine-grained and intricate understanding of the evolution of the organizing efforts of an international network of WikiLeaks supporters is indicative of a long term monitoring of the movement.
Further research by Talk Liberation has uncovered thousands of similar documents including a further 19 documents centrally focused on WikiLeaks. It eventuates that the underlying datasets were constructed by CIA, DoD and Booz Allen Hamilton-connected social mapping experts, profiling a wide range of targets and topics from 2018 up to the present day.
“Modern social network analysis is shockingly powerful, and these NodeXL graphs emphasize that fact. NodeXL bridges the gap between Big Data nonprofits and military think-tanks, being peddled to spy orgs like Booz Allen Hamilton.” – Sean O’Brien, cybersecurity expert and Fellow, Information Society Project at Yale Law School and co-author of #WLDragnet
Marc A. Smith, Director of the non-profit Social Media Research Foundation (SMRF), as well as co-Founder of the for-profit social media analysis consulting agency Connected Action, is the head honcho of the NodeXL social network analysis technology utilized by both organizations and in many of the documents in this release. The SMRF website markets a NodeXLPro package to “Academic/Non-Profit/Government Users”.
Smith spends a lot of time at universities.
For $350 an hour, you can order a consultation with Smith through Connected Action, or for $80 you can order a NodeXL report to be created for you on keywords, hashtags or users you want to track. An automation service means these can be periodically scheduled, or populated from evolving wordlists you nominate or supply.
These keywords form the basis for the collection and are the OSINT (open source intelligence, or publicly available data) equivalent of the NSA’s use of ‘selectors’ – highly specified descriptors that facilitate identifying and tracking individuals.
Our colleague Sean O’Brien has compiled a technical report summarizing our analysis of the NodeXL reports authored by Connected Action. They include periodic automated jobs for at least five major US defense contractors and weapons manufacturers, clearly engaging in reputation management, as well as for NATO events. We have obtained many examples of those automated reports, and categorized them accordingly.
Over a three year period, Marc Smith has run at least 75 NodeXL reports on himself. Anyone mentioning his name, engaging with him or his content, events, or related hashtags, keywords or conversations, is indelibly etched into those maps and filed on NodeXL’s public website.
A ten-year Microsoft Research veteran, Smith’s escapades into profiling, tracking and grouping lists of internet users dates as far back as Usenet in the early ‘00s. In a short 2 minute clip available on You Tube, Smith explains how he was able to ingest all of the data of the Usenet newsgroups network and profile every single individual by their geographic locations, topics of interest, frequency of posts, level of engagement and their interactions with other users. Unredacted email addresses of users appear on his screen during the demonstration.
“We need for there to be a toolkit out there that is open and free and not beholden to any particular set of interests.” – Marc Smith, speaking about NodeXL
NodeXL was developed at Microsoft but according to Smith, “as an experiment” was open-sourced, meaning that when Smith departed Microsoft he was able to take NodeXL with him.
Enter Morningside Analytics. Morningside “discovers and monitors online networks that form around particular ideas”. With $1.1 million in private seed funding, the company was co-founded by its Chief Scientist John Kelly, Ph.D – who had done his Masters thesis with none other than Marc Smith during Smith’s Microsoft days. Kelly “worked on political discussions and how they evolve as networks”. Kelly’s ideology and opinions are outlined at length in this fascinating blogpost, which notes: “Morningside Analytics has clients like think tanks and political organizations” and paraphrases Kelly: “we need to know enough about the actual social network to know who has the power and influence to bring about change.”
Speaking at Neera Tanden’s Centre for American Progress in 2008, five years after Tanden was “central” in founding the institution, Kelly labored to explain how mining online social spaces could benefit the agendas of political institutions. (As of 2021, Tanden is listed as “Senior Advisor” and “Staff Secretary” to President Joe Biden).
In 2013, Morningside Analytics became Graphika. While the registered office address and mission stayed the same, many millions more dollars in private venture capital funding poured in as did new executives and key staffers – including 30-year CIA executive Chris Bane, profiled here in WikiLeaks’ ICWatch.
Within a few short years Graphika would be at the center of a string of US-intelligence connected misinformation and disinformation controversies, from supplying Russiagate and Internet Research Agency analysis to US Congressional hearings and investigative committees, to the UK-based campaign to smear Jeremy Corbyn and disrupt his leadership of the UK Labour Party. Extensive reporting by The Grayzone unmasked Graphika as a Pentagon contractor and greatly contextualizes Graphika’s penchant for converting their social media-based reporting products into political influence, government contracts and cash.
Kelly isn’t Marc Smith’s only tie to Graphika. Graphika Chief Scientist and Russian national Vladimir Barash is on staff at Smith’s Social Media Research Foundation; is an associate at Smith’s for-profit Connected Action, and literally wrote the chapter on Twitter analysis in a book for NodeXL.
Barash also likes to write ideological love letters to Hillary Clinton and Alexei Navalny. “I’m sorry I didn’t do more to help her become President” Barash publicly writes of Clinton. “Like she, I refuse to back down. I will not be silent about my beliefs. And I will follow her example…”
“I’m sorry I didn’t do more to help her become President” – Graphika Director Vladimir Barash wrote about Hillary Clinton
What precisely constitutes Clinton’s example is very much in the eye of the beholder: whether one is from New York State, or from Libya. Whether one is Debbie Wasserman Schultz or Julian Assange. Pussy Riot, or Juannita Broderick.
The NodeXL Graph Gallery is a public dump of social network maps authored by many different NodeXL contributors. The vast majority are authored by Smith’s for-profit Connected Action and his non-profit Social Media Research Foundation. The NodeXL Graph Gallery has 180,000 missing files, as all graphs dated earlier than December 29, 2018 have been scrubbed. Since then, another 84,811 have been added, 1,365 of which are part of the #WLDragnet repository.
Much like computers, mobile phones and the internet itself, tools like NodeXL can better facilitate communication between users, or cause them grievous harm, depending upon the real world application of the technology. Our computers let us talk to each other, but to a hacker, cyberstalker or botnet, our devices are converted into a vehicle to cause us torment, harm and financial loss. Mobile phones can be used to call your mother, or call for help in an emergency. Yet they are also used by militaries to track targets for assassination by drone strike. Innocent or guilty, there are countries on this earth where possessing a mobile phone or being in proximity to the wrong person who does, can get you killed.
People meet and form relationships through the internet; couple, wed and bear children because of the internet, and in some cases, die because of the internet.
This publication is not merely about NodeXL the tool, the technology, or even social network analysis as a discipline – it is about the practical application of NodeXL and that is a reflection of the hands that wield it in any given moment. As proven in this study there can be very real-world harms.
For the drag-netting of supporters of Assange is not without consequences.
“I knew early on that I must be on a watch list. They said I was a Russian agent, which is hilarious, because I don’t speak or understand any Russian.” – WikiLeaks supporter B, named in the NodeXL Embassy expulsion graph, speaking on condition of anonymity
200 Twitter accounts are named in the Embassy expulsion NodeXL chart of April 11, 2019. There are names you will recognize. Names you will not recognize. And names that you would expect to be on the list, that do not appear.
The first step in our analysis was to track how many times each Twitter account appears in the document. Below are the first 41 results. The full original NodeXL document can be reviewed here.

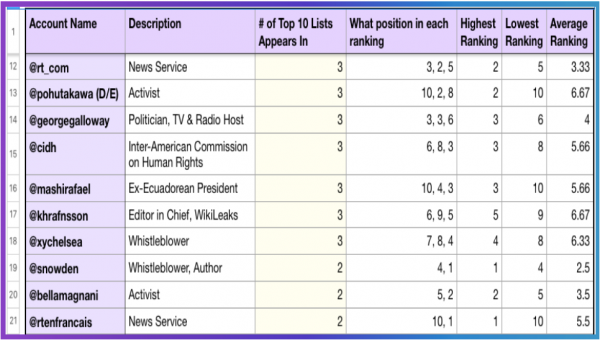


Ranking by effectiveness rather than prevalence is even more useful. Calculating the average position in each Top 10 list held by each account referenced, then sorting accordingly.
Doing so draws conclusions that are closer to what a casual observer might expect: for example, Lenin Moreno moves down in relevance and Edward Snowden moves up – from number 18, to number 2. (Note, in the below chart, news organizations have been separated out)

The options for statistical analysis of the material we are publishing are almost endless, and we are providing this #WLDragnet open public repository precisely to facilitate further discovery by journalists, media organizations and other interested parties.
A fascinating point of note: regular supporters who aren’t well known and have low follower accounts, intermingle in the rankings with high follower influencer accounts. This is because an account’s betweenness factor, where they are acting as a bridge between communities rather than a hub, makes them more significant to the social network than being part of a generally closed group, but with a high follower count
In his public appearances, Smith routinely elaborates on this: “…network theory offers us different definitions of prominence… In fact, it has four or five or six definitions of the word centrality. Do you mean being center in the terms of having the most number of connections? We call that popularity or degree centrality. People with lots of followers tend to have lots of connections. But there are other notions of centrality, more important notions of centrality. How much are you the only person that might span different clusters? We call that betweenness centrality.”
Without these bridges, groups would remain apart.
Therefore bolstering those bridges, strengthens the network.
Burning those bridges, atomizes the network.
“I had to take a step back because of the mental strain and the effects on my relationships. I felt like I was being watched. You know something’s there but you can’t prove it. You know things are happening around you but you can’t do anything about it. It makes you feel like you’re going insane. I can’t explain to you the stress that this has caused.” – WikiLeaks supporter C, named in the NodeXL Embassy expulsion graph, speaking on condition of anonymity
It was clear that it was time to find out what the greater purpose of constructing these NodeXL charts was. Watching countless hours of Marc Smith’s presentations online, revealed much.
Wading through endless NodeXL teach-ins, speaking events and conferences, some general themes emerge. Appearing at universities across America and beyond, Marc Smith’s full presentation format is approximately two hours – 90 minutes of advanced graph theory and applied mathematics, followed by 30 minutes of ideological grooming in a crescendo, the climax of which is brazen recruitment.
The practical modern context Smith argues to bequeath relevance to his academic discipline of choice usually comes down to two main events: the Occupy movement, and Tahrir Square. In a video which is a fairly typical performance of Smith’s, his initial pitch is soft and disarms with light humor. “After 2011, I think we can all agree that 2011 was the year of the crowd, and that crowds have shown their power. There’s almost nothing you can’t do if you and 150,000 of your friends get together… groups of people getting together and expressing their will is becoming easier and easier and more and more consequential. There are several people no longer employed because of this. I’m thinking of Mr. Mubarak right now.”
The first crack at laying groundwork for recruitment is similarly soft. “We seek collaborators who want to use the tool and apply it to their domain.”
The call to action is ego-based and as the position gets harder to justify, the attempts at humor tend to lean towards the absurd. To understand how Marc Smith views NodeXL, its societal role and the true purpose for which he is actively recruiting people around the world into his organization, the following speech is a must-read. Emphasis added:
“We currently have a marketplace of ideas. Social media, hashtags are like stocks for ideas. And what we do not have is an accounting system for the marketplace of ideas and we don’t have accountants and we don’t have auditors. And so, our organization is working on accounting software, social accounting software… and the idea would be, can auditors analyze a hashtag? Can we find evidence of malfeasance, manipulation, collusion, and can those auditors then use this information for some kind of enforcement action and can journalists then turn to this cadre of auditor/accountants, social accountants, data analysts of social media, who are then really becoming kind of like cultural accountants, cultural auditors because they’re the ones who can tell you, is this hashtag’s growth authentic? Are these ideas actually, as they claim, a reflection of a majority’s opinion or are these in fact the amplified opinions of a minority? And so in democracy we need to be able to accurately assess the opinions of our fellow citizens… at the moment I think it is true that social media is being used for disinformation, but there is this cheerful opportunity. We’re going to flip on the lights and we’re going to take some photographs and the photographs are going to be this photograph of a hand in the cookie jar with a face. A face, a cookie jar and a hand. The hand will be in the cookie jar. I predict that much like the Pandora Papers is showing cookie jars with hands in the cookie jar with a face, those three elements are very critical… could we use those kinds of techniques to make it harder to inject low quality information into social media? Yes, I think we can. I think we can use accounting software, social accounting software, and accountants to use it and the journalists to talk to them, to change the discourse… So we would like there to be an army of scrutinizers, of auditors, of cultural accountants..”
Thus, Smith’s vision of the future is one where he and his “cadre” are the self-appointed social and cultural accountants and auditors of the masses; where a majority opinion takes “enforcement actions” against minority opinions and where you and I merely exist to be accountable and to be audited. Smith continues his recruitment pitch: “So what would the marketplace of ideas be like if we had accountants? And that would be you. And what if we had a kind of accounting package for social media, for culture, for the marketplace of ideas, and that would be us. Because we’re not about debits and credits, we’re about from and to.”
“So why does that matter? Because information has consequences. It could be argued that what we have created is an information system, yes, but not necessarily a high quality information system… We have this line in sociology that things are real in their consequences” – Marc Smith, NodeXL
As Smith gets deeper into each presentation, the once-soft rhetoric turned bizarre metaphorical rhetoric turned blatant recruitment continually hardens until the mask of academic political neutrality hits the floor with a thud.
Smith rolls out his favorite slide, seen time and time again in his presentations: with the ominous label “Needed”.
Detect. Deflect. Deter.
Smith explains: “There are three things necessary to essentially domesticate information networks and that is detection, deflection and deterrence. Detection is when you know you’re under attack, deflection is what you do as a result, and deterrence is where you have a reaction so severe that people don’t bother to attack you in the first place.”
“I am outraged by these people describing themselves as “social or cultural accountants. There does need to be an “accounting” for this behavior but by them, not us supporters. Wikileaks and Julian Assange have huge global popularity because people want to be told the truth. The spies have to work so hard to track, deflect from and undermine that popularity but it is not going to go away.” – @BellaMagnani, WikiLeaks supporter named in the NodeXL Embassy expulsion graph
Depending on which audience Smith is speaking to, you get a different story about this slide. His choice of language shifts from bombastic and inflammatory (such as at the SMART DataSprint) to diminutive and tentative.
When he’s concerned about appearing too militaristic, the bluster is significantly toned down and he tells the audience: “And then of course, there is deter. And I put a question mark here because it’s ethically dubious. But deterrence goes, the thing you just did to me? I’m going to do it to you. So maybe you shouldn’t do it to me anymore. And that’s deterrence. Americans love deterrence, we’re really into deterrence. So I’m going to leave that with a question mark, because I don’t know that its ethical to come up with offensive technology that causes a social media chaos and the proliferation of misinformation but I do believe that detection is a wholly ethical direction for scholars and researchers.”
Now meet Marc Smith, unleashed:
“If I tell you you are being attacked right now, what do you do about it? Then what? Then of course deterrence is the idea that, if Mr. Putin is sitting there going, hey hey, we’re going to mess up American politics more, we say, would you like to see Mr. Navalny become a cult leader? We can make that happen. Maybe you would like to back down then. Because in the same way we have mutually assured destruction on the nuclear weapons front, we would have some kind of mutually assured destruction on the social media epistemological battle front.”
In Marc Smith’s world, democracy is constantly under attack and the solution is to engage in increasingly anti-democratic actions in violation of democratic norms, in order to preserve democracy. This is eerily reminiscent of the invective frequently heard from heads of intelligence agencies, politicians and military leaders. The following quote from Marc Smith could as easily have been issued directly from the White House, State Department or Pentagon: “We also don’t want to be leaving the castle gate open when the enemy is at the gates. We need to find a balance somewhere that does penalize low quality and dangerous speech while enabling the diversity of speech that we want. So it is the case that social media makes a promise that all may speak but it does not make a promise that all may be heard.”
The problem is, of course, that if you say something on social media that the powers that be feel affronted by, you certainly will be heard. While the technocracy may choose to restrict your ability to project messages to other citizens, to limit or inhibit your communications with your peers by various methods (think: shadow-banning, account suspensions, etc) what they never concede is their own ability to monitor your every keystroke.
But it is more than keystrokes being monitored.
“It’s very frustrating how mainstream media pretend all this is just “conspiracy theory” even though they themselves publish stories about US or UK governments spending millions on cyber propaganda. When it gets to the point where it is affecting people around me, I just shut down and switch off for a while. But ultimately we are all in this fight because Julian Assange’s freedom is our freedom too. If WikiLeaks is not allowed to publish the truth then who will? How does the world solve problems if we don’t even know the basic facts?” – @jaraparilla: a WikiLeaks supporter named in the NodeXL Embassy expulsion graph
As we began systematically interviewing WikiLeaks supporters who are named in the #WLDragnet files a pattern of real world monitoring, in retribution for their online dissent, was evident.
Asked simply, “Have you had any adverse experiences online or in the real world that you believe are tied to your actions in support of Julian Assange and WikiLeaks?” respondents described a range of shocking incidents, including:
Indicators of physical surveillance:
- People taking photographs of WikiLeaks Supporter A from vehicles
- WikiLeaks Supporter C being tailed on the streets “all the time”
- WikiLeaks Supporter D being followed and openly monitored by strangers, “military types”
Indicators of digital surveillance:
- Remote corruption of devices, both hardware and operating systems
- Network and signal disruptions at key moments
- Devices switching off or powering down of their own accord
- UI (User interface) anomalies, device glitches (devices operating abnormally)
- Battery power draining inexplicably quickly
- Strange sounds, interference on telephone lines
“I think I felt like I was going crazy.” – WikiLeaks Supporter D, named in the NodeXL Embassy expulsion graph, speaking on condition of anonymity
Sustained online harassment campaigns:
- 100% of respondents reported having been targeted online by networks of troll accounts
- 60% of respondents reported having been the target of smear blogs that published defamatory and false accusations about them, as well as personal information
Interference with their social media accounts:
- Follower counts and statistics frozen
- Content inexplicably removed without notice
- Accounts lockouts
- Arbitrary account suspensions
Respondents spoke repeatedly about the impact on their mental health:
- Experiencing profound stress, feeling under duress
- Feelings of profound isolation
- Feelings of confusion and self-doubt
- Deleterious effects upon personal relationships
Respondents spoke about financial loss, interruption with their ability to work and earn income to support themselves in ways they otherwise would usually have been able to, with one respondent raising the issue of “the financial grief that you’re caused from not being able to make ends meet because of the pressure applied.”
“I felt alone in it, because I would sense these things were happening, but I had no one to share it with or relate it to so I felt really alone in the world about it. I knew it was going on with other people, with people’s accounts being demonetized or suppressed, what I took out of it is that I must be hitting them where it hurts here, I must be doing the right thing, so it was a little bit encouraging as well, but not nice obviously.” – @humanidee, WikiLeaks supporter named in the NodeXL Embassy expulsion graph
WikiLeaks Supporter E spoke of a high level of maliciousness to the narratives circulated about them by the troll accounts who attacked them online: “I’ve been a very vocal supporter for a long time because I saw from the start that the Swedish investigation was a fraud, and what its real purpose was. I spoke out as a woman who had also reported rape to the police, with a very different experience of how seriously the authorities took me, and I got targeted by mobs of trolls on that basis. It is appalling that these groups paying for NodeXL surveillance would descend to such gutter levels against a woman who saw through the lies and spoke out in defense of Julian Assange.”
Most alarming of all was those WikiLeaks supporters who to this day feel so paralyzed by fear that they remain unable to speak freely about their experiences. WikiLeaks Supporter F confided an awareness that they prefer to chalk things up to coincidence as an internal defense mechanism, in order to be able to cope. This is entirely understandable, albeit heartbreaking. For some, to even try to consider a wider picture of what is occurring in the moment, or the subsequent far-reaching implications thereof, presents a risk of trauma in and of itself. WikiLeaks Supporter G refused to confirm or deny whether they’ve been targeted. They listened keenly to what others had been experiencing, but when it came to their own situation, they immediately clammed up, even when promised that anything they shared could remain anonymous.
For these everyday citizen supporters of WikiLeaks, the fear is real. And with Julian Assange being made a prime and very public example of, the fear is both logical and justified. There are no guidebooks to prepare new activists for what they will face, nor are there sufficient resources to support them if and when they become targeted. Activists don’t have resilience training, adequate forewarning or sufficient resources to be able to meaningfully defend themselves against the immense forces that many find themselves up against. Lives are destabilized, relationships and careers destroyed and worse, on a daily basis. Ask any veteran of a sizable social justice campaign what they have experienced over the years and decades and they will have uncountable war stories. And it is war. It is a war being waged upon innocent civilians, by their own governments.
“I’m horrified, disgusted and flattered in equal measure. This is what they’re doing to people who are telling the truth. If we don’t know the truth now, about things that are happening now, how can we know the truth about anything in history. Our whole history could be a lie. And this is why they’re trying to keep their secrets. This is why they’re being so active against people who are telling the truth. We do what we do but Julian’s taken the brunt of it. What we’ve faced is nothing compared to the torture he’s faced.” Gordon Dimmack, independent journalist named in the NodeXL Embassy expulsion graph
(In years past, co-author of this work Suzie Dawson wrote extensively of her experiences being targeted by private and state surveillance agencies hell bent on suppressing her work. Although the methods of repression described by WikiLeaks supporters named in #WLDragnet are hauntingly similar, and indeed Dawson and movements she was pivotal in appear repeatedly in the keyword lists of the NodeXL graphs in the #WLDragnet files, her experiences are not included in the anonymized data that is presented above.)